In an exclusive interview to Telecom Review, Moiz Baig, cyber security advisor at Nokia MEA talks about different aspects of 5G security: challenges, best practices and frameworks, “zero-trust” approach, and guaranteeing a secure 5G network for customers.
5G has gained a strong traction among the leading operators across the globe including in the Middle East and Africa. At this juncture, what are the main security challenges of 5G networks Nokia sees, being an expert in network security space with advanced security solutions?
It is estimated that billions of devices will be connected to the 5G network in the coming years. Many of these devices will be low power sensors, wearables and small devices used in various industries. 5G increases wireless capacity by 1000 times, connects 7 billion people and 7 trillion Internet of Things (IoT) with zero perceived down time.
Realizing network as a service and the diversity of 5G use cases will make securing the network more complex. Availability, confidentiality and integrity of all users as well as management and control functions need to evolve to cater to: dynamic networks, multiple players involved in service delivery, wide variety of devices (including IoT), users and applications.
Multiple logical networks, so called network slices, will be running on the shared 5G infrastructure. This complexity leads to a large attack surface. Moreover, the huge number of connected devices also means that the network may be exposed to massive attacks by such devices, and they become infected by malware and abused by an attacker as a botnet for carrying out attacks such as distributed denial of service (DDoS) attacks. With 5G, vulnerabilities in the network may have more serious consequences than was the case with previous generation telecom technologies due to diversity of use cases. In addition, the convergence of telecom and IT infrastructures, services, and operations, require a more holistic and broader look at 5G security than before.
How can the security of 5G networks be guaranteed? What are the best practices and frameworks that can be adopted?
5G networks must support a very high level of security and privacy for their users (not restricted to humans) and their traffic. At the same time, networks must be highly resilient to all kinds of cyber-attacks. To address this two-fold challenge, security cannot be regarded as an add-on only; instead, security must be considered as part of the overall architecture and built into the architecture right from the start. Based on a secure architecture, secure network function implementations are also essential to ensure a high security network. Security assurance methods are therefore crucial so that operators can ensure the required security level for different network functions.
5G networks complying with the 3GPP security architecture will provide multiple protection measures, including:
- Authentication and authorization mechanisms between network and devices and between network elements of a single or different network.
- Cryptographic protection of traffic on the various network interfaces.
- Temporary identities and concealed identities to hide the subscribers’ permanent identities in the communication over the radio interface.
- Secure environment inside the (physically exposed) base stations to ensure a secure boot and protect sensitive data.
A “zero-trust” approach is often considered as the best security concept in 5G. Do you agree?
The importance of having a zero-trust approach in 5G is crucial given the vast majority of critical use cases it aims to address impacting both humans and industries alike, however, given the built-in layered security associations within 5G, the needs for zero trust is reduced.
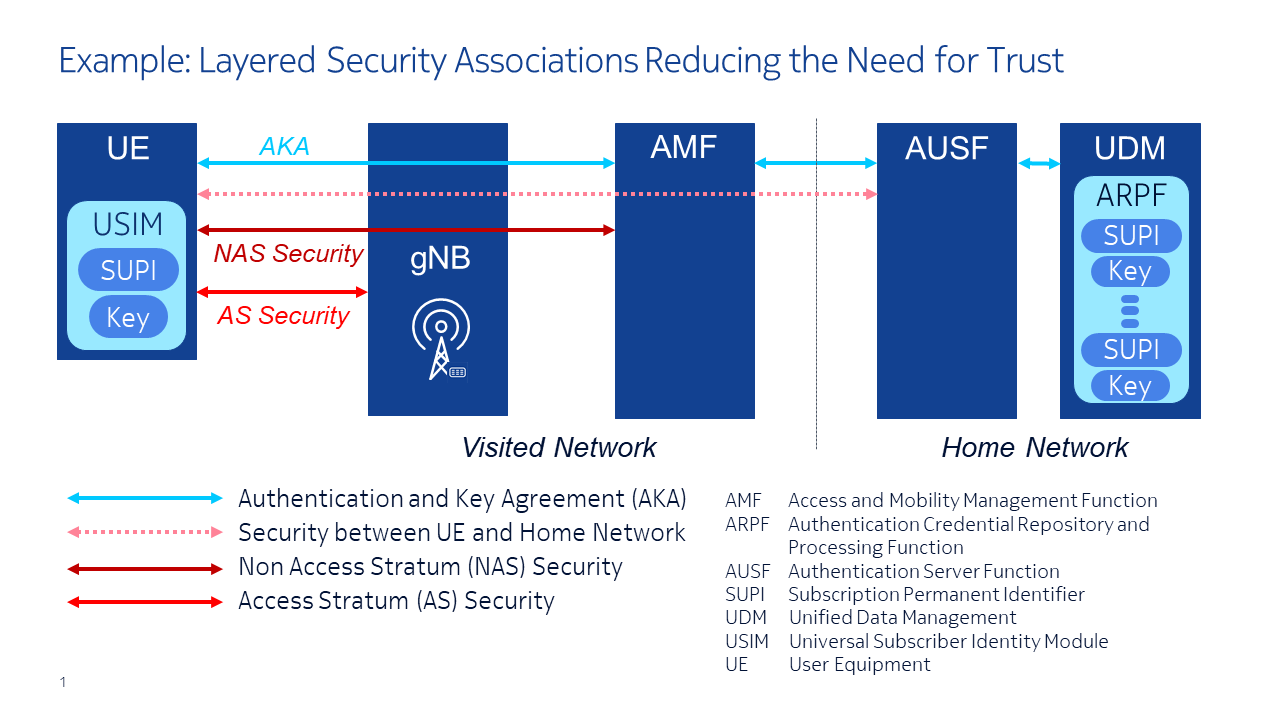
The 3GPP 5G framework defines network security features supporting a zero-trust architecture approach in the three key domains: network access security, network domain security and service-based architecture (SBA) domain security.
The network access security features provide users with secure access to services through the device (user or an IoT device) and protect against attacks on the air interface between the device and the radio node.
Network domain security includes features that enable nodes to securely exchange signaling data and user data, for example, between radio and core network functions.
The 5G SBA is built on web technology and web protocols to enable flexible and scalable deployments using virtualization and container technologies and cloud-based processing platforms. SBA domain security specifies the mechanism for secure communication between NFs within the serving network domain and with other network domains.
How can Nokia assist in securing its customers’ 5G networks?
Most of the new security functions that are defined in the standards are mandatory to support, and optional to use. Vendors are required to implement mandatory 3GPP defined security features. However, due to a variety of reasons (e.g. operator budget restrictions, different legislations in different countries, risk acceptance exercises) some network operators are not using or configuring the security functions available to them thus, weakening network security.
This can expose the network and its users to unnecessary risks. Operators should conduct a risk assessment justifying the adopted security decisions. Reporting of such decisions may also be part a regulatory requirement.
Nokia Security Advisory Services is helping its customers address complex security challenges while rolling out 5G networks in accordance with global and regional regulatory security requirements, addressing the skill gap that exist particularly in the ability to assess 5G security controls.
Key deliverables of security advisory services are listed but not limited to the below:
- Joint security assessments across customer teams to build a current security profile based on established frameworks.
- Advice for design, architecture and implementation, hardening against regulator telecom security framework and compliance.
- Mapping of security controls to regulatory and global framework compliance such as NIST and 3GPP NESAS.
- Tangible recommendations based on target profile creation across all domains of a 5G network to be able to close 5G security gaps that may exist.
In the end, the customer benefits from a newly established 5G security baseline across its network domain, having a clear view of the potential gaps in its 5G security posture and visibility, and mitigation of security issues.










